💡 Cybersecurity Research Brief: The Calendar Phishing Threat
This report breaks down the growing risk of Calendar Phishing—a new attack that targets your employees, bypassing traditional email filters and exploiting the trust you place in your digital calendar.
1. How the Scam Bypasses Your Defenses
Calendar phishing works because it uses a function of your calendar app (like Outlook, Microsoft Teams, or Google Calendar) that is often a security blind spot.
The Core Trick: Auto-Add
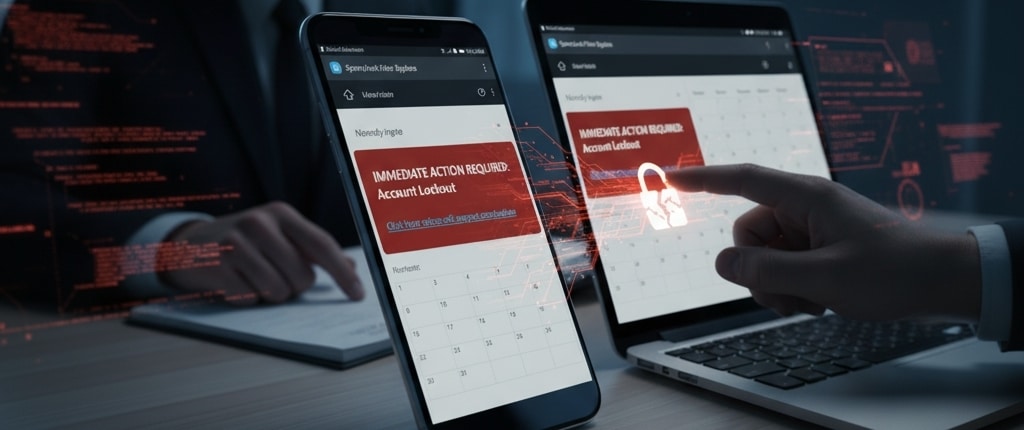
- Invisible Entry: A criminal sends a fake meeting invitation using the standard calendar format.
- Bypassing the Inbox: Because your calendar software (especially Outlook and Google Calendar with default settings) is often set to automatically add any invitation you receive, the malicious event skips your spam folder and lands directly on your schedule.
- The Hidden Payload: The event itself uses urgent language like “Immediate Account Termination” or “Microsoft 365 Action Required.” The description or the conference link contains a malicious web address that leads to a fake login page designed to steal passwords.
Why Teams is a Target
Attackers are increasingly using Microsoft Teams invites. Since Teams processes these events through internal services, the invites can completely bypass the security checks applied to normal email. The threat appears directly in your calendar, sometimes followed by a fake “IT Support” call in Teams, tricking users into installing harmful software.
2. The High Stakes: Business Risk for Owners and Management
This attack is highly dangerous because it relies on panic and trust, leading to three major business consequences:
- 🔐 Credential Theft: The primary goal is to steal your Microsoft 365 or other account passwords. A stolen login can lead to Business Email Compromise (BEC), where criminals impersonate you to commit wire fraud or divert payments.
- 🦠 Malware Infection: The links in the calendar invite can lead to sites that secretly download viruses or ransomware, shutting down your entire operation.
- 🤯 User Panic & Distraction: The urgent, official-looking alerts about account termination cause employees to panic and click the link immediately, often without thinking or following established security protocols.
3. The Employee Action Plan
Protecting the business from calendar phishing is a matter of changing habits and adjusting settings.
| Action | Why This Works |
| 🛑 DO NOT INTERACT | Never click the link, open an attachment, or try to join the meeting. |
| ❌ DO NOT DECLINE | Clicking “Decline” or “Accept” confirms to the scammer that your email address is active, increasing future attacks. |
| 🗑️ DELETE Manually | Right-click the event directly on your calendar and select Delete/Remove without opening it. |
| 📞 VERIFY Separately | If the invite seems legitimate, do not use the link in the invitation. Instead, open a new browser window and navigate directly to your account’s official website to check for alerts. |
| 🚨 REPORT IT | Notify your IT team immediately so they can investigate and block the malicious sender. |
4. Closing the Security Gap: Our Advanced Cybersecurity Services
As a business, you shouldn’t have to rely solely on your employees to manually spot these sophisticated scams. Our services are designed to address the deeper, systemic mistakes that leave SMBs vulnerable.
We provide a comprehensive layered defense to automatically catch what human eyes might miss:
- Advanced Phishing/Spam Detection: We implement and manage superior security tools that go beyond basic email filtering to detect malicious content hidden within calendar invites, attachments, and links, stopping the threat before it hits your employees’ calendars.
- Managed Security Solutions: We proactively manage your security configurations, including setting up and enforcing Multi-Factor Authentication (MFA) and disabling risky default settings (like the automatic calendar-add feature) across your organization.
- Cybersecurity Training & Testing: We provide targeted training that focuses specifically on emerging threats like calendar phishing and Teams-based scams. This is reinforced with regular, realistic phishing testing of your employees to measure their awareness and ensure your people are the strongest line of defense, not the weakest link.